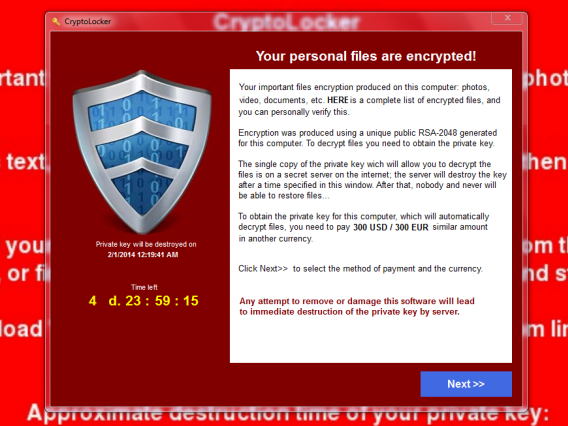
The traditional way of coming home to access the internet, email and social media has gone out the window. While home based security is critical, it also needs to take into account your mobility.
Like a King who is relatively safe in his castle with its layers of security, once he leaves the castle, the security has to change.